Identity management: SSO + user provisioning in LogiqcQMS for Microsoft Entra ID
This article provides background information required to plan the implementation of Single Sign On (SSO) and user provisioning. It also contains a link to the SSO configuration manual.
Single Sign On (SSO) with User provisioning is an additional add-on, available as part of the Logiqc Enterprise Plan. It is only available for organisations that use Microsoft Entra ID for identity management.
Logiqc SSO supports single and multi tenant Entra environments
Contact us if you are interested in learning more about this product.
About the implementation process
Background information of the SSO implementation process
To implement SSO and provision your Logiqc users, your IT Admin will create a Logiqc Enterprise application in your organisations Active Directory. They will connect this application to your Logiqc platform. User accounts added to the enterprise application will be provisioned into the platform. Once they are provisioned, users will authenticate into the platform via their Microsoft user account.
Implementing SSO and provisioning your users does not require any system down time. You can schedule the implementation at a time that suits your organisation.
The configuration steps are set out in the configuration manual which you can download via the link at the bottom of this article.
Once you have implemented SSO, you will no longer need to manually create user accounts in the Logiqc platform. New user accounts will be provisioned into the platform via the Enterprise application. A Logiqc administrator will activate newly provisioned accounts and set them up with their appropriate access.
Pre implementation steps
The following are recommended steps you should take prior to implementing SSO and User provisioning.
- Create an external administrator account for the person (IT Admin) who is responsible for managing your Entra ID environment and provide them with the SSO configuration manual.
- The external admin account requires the following permissions:
-
Edit System settings
-
Edit API keys
-
Create and edit users, roles, and teams
Setting up an account for external administrators and auditors -
- Provide a list users from your organisation who require access to the Logiqc platform to the IT Administrator.
Note: Ensure your IT admin only provisions these user accounts and not other Active Directory objects such as fax machines, printers etc. Accounts added into Logiqc cannot be deleted. - Provisioning existing Logiqc user accounts:
- Check all current Logiqc user accounts to ensure these accounts all have a valid and unique email addresses.
- Ensure no users are sharing the same email address – e.g., reception@ admin@.
- Ensure users email addresses in their Logiqc user accounts are an exact match to their Microsoft email address.
- Clean up your user account list by deactivating any old user accounts you won’t be provisioning.
- Provisioning new Logiqc user accounts:
There is no need for you to manually create new user accounts in the Logiqc platform before implementing SSO. The process of adding new users will be handled by your IT admin through the user provisioning process covered in the SSO configuration manual.
Post implementation of SSO
Below is information you will need to be familiar with once SSO has been implemented.
- New Logiqc user accounts – When new user accounts are provisioned into the Logiqc platform, they will be inactive. Click on this link for instructions regarding activating provisioned user accounts.
- Existing Logiqc user accounts – After provisioning existing user accounts, these users will be able to authenticate themselves by using their Microsoft user account when accessing the Logiqc platform. This means they no longer need to log into the platform using a local Logiqc username and password.
- Adding new users once SSO has been implemented – To add new users to your platform, your IT Admin will add their Active Directory account to the Logiqc Enterprise application in Active Directory. Once provisioned, the account will have an inactive status in the Logiqc platform and will be marked as 'Awaiting activation'. The account is now ready to be activated. Click on this link for instructions regarding activating provisioned user accounts.
- Removing users once SSO has been implemented – Your IT Admin will remove your user from the Logiqc Enterprise application in Active Directory. This will deactivate their Logiqc user account preventing access to the platform.
- External user access post SSO implementation. – For external users such as auditors or network administrators who won’t have access to Logiqc via SSO, local accounts can be added using the external user licence. Once these accounts have been set up, the user must access Logiqc locally. To log into the platform locally, add "/login" to the end of your Logiqc URL. E.g. https://YOUR_URL.logiqc.com.au/login. This will take the user to the Logiqc login screen where they will login using the Logiqc username and password that has been provided.
Troubleshooting
Implementing Single Sign-On and provisioning your users is a straightforward process, and our manual outlines all the information and steps required for a successful implementation. However, we recognise that details can occasionally be overlooked, so this section highlights key points in the setup to help ensure a smooth and successful implementation.
-
Admin permissions required to set up single sign on and user provisioning in the platform
-
Edit System settings
-
Edit API keys
-
Create and edit users, roles, and teams
-
- Enabling SSO
- Once you select ‘Enable SSO’ and save this setting, users will no longer be able to log in using their local Logiqc username and password, and must access the platform via SSO.

- Local admin login. If your IT admin needs to log in locally after SSO has been enabled, add '/login' to the end of your Logiqc URL: e.g.: https://housing.logiqc.com.au/login
- Once you select ‘Enable SSO’ and save this setting, users will no longer be able to log in using their local Logiqc username and password, and must access the platform via SSO.
- Platform system settings check-Admin>System settings>General settings

- The ‘Enable user provisioning through SCIM’ setting allows you to automatically provision users from your Microsoft Entra environment into Logiqc.
- Selecting ‘Enable SSO’ turns on Single Sign-On. Users will then only be able to access the platform using their Microsoft email address and password.
- Client ID. This is your 'Application (client) ID' from Entra.
- Authority. Ensure you include the correct authority URL (https://login.microsoftonline.com/), followed by your 'Directory (tenant) ID'
- API keys

- Make sure you set expiry date to 'Never'
- Add the IP filter - 40.126.0.0/18,20.190.128.0/18
- Do not apply a rate limit.
- Checking user provisioning status
- New users:
- Go to Admin mode select Users
- New users:
-
-
- Toggle on 'Show inactive'
- Set filter to 'Awaiting activation - Yes'
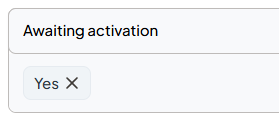
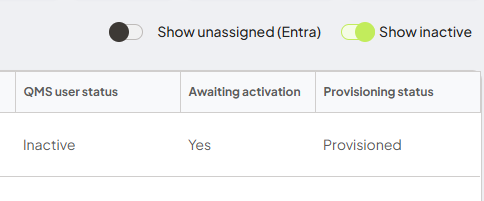
- Check status is 'Inactive', 'Awaiting activation - Yes', Provisioning status is 'Provisioned'. Account is ready to be set as active
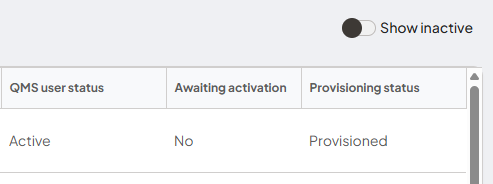
- Existing users
- Go to Admin mode select Users
- Status is 'Active', 'Awaiting activation' is 'No', Provisioning status 'Provisioned'
-
SSO and User provisioning manual
Click on the image below to download the SSO and User provisioning manual.
Reminder: SSO is a paid add on and must be configured in your platform before you will be able to implement this feature.
doc_674 v10 (Last updated 13/02/2026)
Configure Entra for mobile
To enable users to log into the Logiqc mobile app using Single Sign-On (SSO), you need to configure Entra to support mobile devices. Here is an article explaining the steps: